Post-Quantum Cryptography moves from “later” to “now”: What ASD’s new Cyber Threat Report means for Australian organisations
Australia’s cyber threat landscape is accelerating on all fronts, from state-sponsored targeting of government and critical infrastructure to the rising financial impact of ransomware and data breaches. The Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) has released its Annual Cyber Threat Report 2024–25, and one message is crystal clear for boards and technology leaders alike: start preparing for post-quantum cryptography (PQC).
Why PQC is now a board-level priority
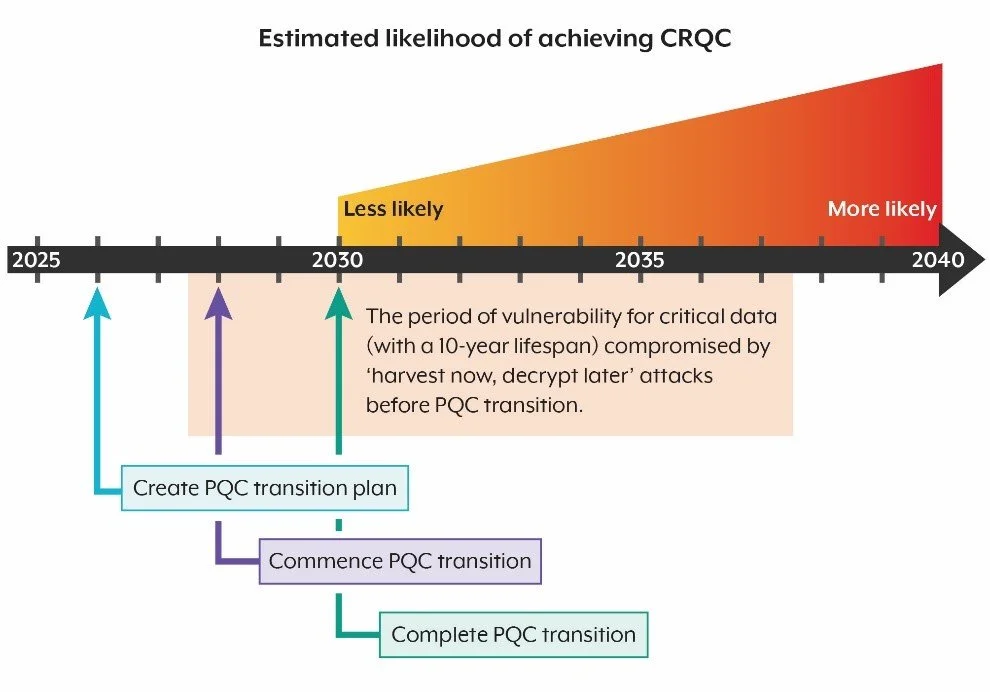
A cryptographically relevant quantum computer (CRQC) could break today’s widely used public-key cryptography (e.g., RSA and ECC). That creates “harvest-now, decrypt-later” risk for data with a long confidentiality shelf life (health, finance, IP, national security). ASD’s updated guidance frames PQC as the best path to protect networks and data in a quantum future, and signals a shift from awareness to action.
Key signals from ASD’s 2024–25 report
Threat volume and impact continue to climb. Over FY2024–25, ASD’s ACSC received 42,500+ hotline calls (↑16% YoY) and responded to 1,200+ incidents (↑11% YoY). Proactive notifications to entities jumped 83%, underscoring both attacker activity and improved national visibility.
Four “big moves” to uplift resilience include: implement effective logging, replace legacy IT, manage third-party risk, and critically, prepare for post-quantum cryptography.
What “prepare for PQC” actually means
ASD’s recent Planning for Post-Quantum Cryptography guidance outlines a practical transition path and urges organisations to begin now, given multi-year change cycles across assets, vendors and supply chains. Key takeaways:
Create a crypto inventory
Map where public-key crypto is used (protocols, products, certificates, devices, apps, third parties). Prioritise systems with long-lived data and long replacement cycles.Adopt a crypto-agile architecture
Build the ability to swap algorithms and parameters without major redesigns (e.g., through abstraction layers, policy-driven selection, and standards-aligned libraries).Run pilots and parallel testing
Trial PQC algorithms in controlled environments, validate performance and interoperability, and plan dual-stack approaches for transition windows.Refresh supplier requirements
Update procurement and SLAs so vendors must support ASD-aligned PQC and crypto agility; verify upgrade roadmaps (firmware, HSMs, IoT/OT, network gear).Plan your cutover sequence
Sequence high-value use cases first (VPNs, TLS, code signing, PKI, backups/archives), then broaden to enterprise-wide crypto refresh. Align with ASD’s ISM and Essential Eight.
How Quantum Australia can help
Quantum Australia’s Partnerships Program connects quantum capability to real-world impact, helping organisations understand how quantum and quantum-adjacent technologies, like post-quantum cryptography, can strengthen cyber resilience. Through our national network of Partnership Managers, we help organisations map their quantum-readiness journey, connect with researchers and technology partners, explore use cases in secure communications and data protection, and access grants and pilot programs. We also support workforce development and startup growth to ensure Australia builds the talent and capability needed for a secure, quantum-ready future.